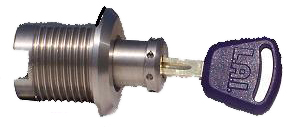
Protecting Your Gas Dispensers From Skimmers
Over the past decade, identification thieves have been taking advantage of the widely available and easily copied universal keys that lock up most gasoline dispensers. They open the access door to the reader and attach a skimmer, which transmits credit and debit card data to their team. Usually, the theft is detected long after it. Read More »
Strengthening the Weakest Link in Your Security Chain
A few years ago, I published an article that compared self-storage security to a chain, a chain that was only as strong as its weakest link. A string of facility break-ins throughout the last year have demonstrated what I meant: Every component in the following stories works to some degree, except the lock, which results. Read More »
Key Control and Data Security: Protecting Your Customer’s Files
Rich Morahan recently spoke at the NAID Conference in Miami about the role key control plays in protecting client data files. The presentation was well received and we would like to thank all those in attendance. As a courtesy to those who attended and those who were unable to attend we have made the PowerPoint. Read More »


|

|

|

|

|

|

|



.jpg)